In this blog post, I want to talk about risk management and the concept of threat modeling. Let’s start with some basic math, then dive into definitions and some examples.
Definition of Risk
Risk is the multiplication of vulnerability and threat. As with all multiplications, to lower the product (risk in this case), you need to reduce the factors (vulnerability and threat in this case). There is no such thing as zero risk because no one is free from vulnerabilities or threat free. Each one of these can be approaching zero, but they can never be zero. So, risk management aims to get it as low as possible, not to eliminate it.
Definition of Vulnerability
Now with the math out of the way, let us dive a little deeper.
For a definition of the term vulnerability, we turn to dictionary.com as the English definition works perfectly here. You could say we are switching from match to English.
adjective
- Capable of or susceptible to being wounded or hurt, as by a weapon: a vulnerable part of the body.
- Open to moral attack, criticism, temptation, etc.: an argument vulnerable to refutation; He is vulnerable to bribery.
- (of a place) open to assault; difficult to defend: a vulnerable bridge.
From this definition, it should be clear why there is no such thing as zero vulnerability.
Definition of Threat
Now let us talk about the concept of threat and threat modeling. From dictionary.com again:
Threat noun
- an indication or warning of probable trouble: The threat of a storm was in the air.
Threat Model
A threat model is simply a catalog of all the threats that could possibly come up. This is something that can be written down or not. It requires no justification, is very personal and subjective. If you feel something is a threat to you, include it in your catalog. No one else gets a say in what is included in your threat model. A good threat model covers all aspects of someone’s life. It should cover personal aspects, work aspects, and both online and offline threats. A threat model can be done at various levels. You can have a personal threat model, another one for your family, and the third one for a group you are responsible for. When creating a threat model for more than just yourself, it would be appropriate to consult those included in the model. While you may be consulting with others on a threat model for a group, this should be a judgment-free exercise. For more details on threat modeling, check out my book, or reach out for an engagement to help lead you through it.
Details makeup of a threat
Now let us dive into more details about a threat.
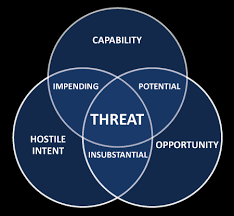
A threat has three components or concepts. Any avid crime mystery fans should be very familiar with these: motive, means, and opportunity. When dealing with threat modeling, it is more commonly referred to as capability, intent, and opportunity.
Capability
The term capability refers to having the ability to do something. This ingredient is present in most of the cases involving threats to our physical wellbeing. Most of us possess the physical ability to do unspeakable harm to another living creature. Luckily, most of us are decent human beings who could never even imagine harming another person.
In other words, we lack the hostile intent to harm others. Going back to capability, when it comes to online threats, this element is frequently missing, as it requires a good deal of technical knowledge for someone to be a menace online. So those without technical knowledge lack the capability to be a threat online. Regardless of how much they desire to be a menace, they can never become a real threat online until they gain the required technical skills.
Opportunity
Opportunity is the concept of having access to something. It’s about being in the right place at the right time and with access to the target. In the physical world, this means having access to the person you wish to harm. Personal bodyguards and diplomatic protection details rely heavily on removing opportunity from the equation to keep the person they are protecting safe from harm. They can’t control a person’s intent, nor can they control a person’s capabilities; however, they can manage opportunities. As we discussed, there is no threat without all three components. By controlling public access to the person they are protecting, they limit the opportunity factor, thus limiting the threat and the risk.
Intent
The last element is the concept of intent, sometimes called motive or desire. If people have no ill will towards you and do not wish you harm, they pose no real threat. Returning to physical protection methods, including bodyguards, the concept of security screening deals in this space. Security screening tries to assess if you hold any ill will towards those who are under security protection.
This can be difficult to determine and can change without any notice or warning. We see this when an initially peaceful place suddenly becomes a hotspot of violence. In most cases, the folks involved didn’t suddenly gain new opportunities or obtain new capabilities. Most of the time, something happens to trigger the mass of people to achieve a newfound desire and motivation to take things into their own hands.
Depending on these ingredients are mixed, you can have four different types of threats:
- Opportunity + Capability = Potential Threat
- Opportunity + Hostile Intent = Insubstantial Threat
- Hostile Intent + Capability = Impending Threat
- All Three = Actual Threat
For those more visually inclined, here is a venn diagram demonstrating this.
This is written in October 2020 while the whole world is dealing with the Covid-19 pandemic and all discussions are around that. So I find it only fitting that use that as another example.
It has been demonstrated that no one is immune to catching Covid-19. How badly it impacts any particular person or for how long seems to vary widely. Everyone is thus vulnerable to Covid-19 but to a varying degree.
At the time of this writing, seven months into this pandemic, there is no cure available. Doctors appear to have gotten better at managing symptoms and increasing survivability, but there is no cure. All we can do is take precautions; this is called implementing compensating controls in the cybersecurity world.
You could completely avoid all human contact, move to a farm in the middle of nowhere, and not have another soul for miles. Just like not connecting a computer to the internet to avoid viruses, this is not a feasible approach for most. Scientists tell us that as long as we avoid being in close proximity to people we don’t know for extended periods, we have minimal risk of getting infected. They define close proximity as less than 6 feet or 2 meters and extended period as 15 min or more. They also advise that wearing a face mask covering both nose and mouth reduces the risk even further, especially when everyone is wearing a mask. So wearing a mask, maintaining distance, and limiting interaction with people you don’t know is a reasonable precaution or compensating controls in geek-speak.
This means skipping going dancing, hanging out in bars, going to the theater, and other places where people congregate for long periods and possibly even extremely close proximity.
Where some people may tripping up with this precaution is how they define what they consider known people. Just because you’ve worked with them for ten years or they are a close cousin of yours doesn’t mean you can treat them as “known people” in this context.
Knowing their favorite food, their favorite movies, how they like to dress, their favorite restaurant might be considered knowing someone well in normal times, but this is useless information in the time of covid-19.
What do you do know about their threat and risk handling? What precautions are they taking? If they aren’t taking any precautions, they could pose a significant threat to you. A family member that is going to all the hot spots, going clubbing on weekends, etc., can have a significant potential risk to you despite you knowing them very well, and it might be wise for you to keep your distance from them. On the other hand, someone you know barely, but you know for a fact that they are taking all the same or more precautions that you are, would be reasonable to lower your guard around them a little.
